Since our first cyber insurance post, serious breaches like WannaCry are making it clear that cyber insurance policies are moving from niche to mainstream.
Vulnerability has become an onion of concern as organizations seek to protect not only their own sensitive data, but also any client data or system connections for which they may be a trustee, such as during e-discovery and other strategic solutions work.
“Modern enterprises are becoming painfully aware that 100 percent cybersecurity is an impossibility,” says Judy Selby, an insurance and strategic cyber risk consultant. “Instead of focusing exclusively on building cyber defenses, smart companies are taking an enterprise approach to managing cyber risks.”
And for many, cyber insurance is a step in that direction.
After our first article, we still had questions about cyber policies. Once a company has a policy in place—then what? (Well, with any luck—nothing.)
1. What happens when a company discovers a data breach?
Legal requirements may vary by location; in the US, 47 states have enacted data breach notice laws, outlining what data are covered, how the state defines a breach situation, who must be notified and how and when, and whether those parties have the right to take action against the company.
The company may be responsible for covering the cost of credit monitoring and/or restoration services for individuals who’ve been potentially impacted.
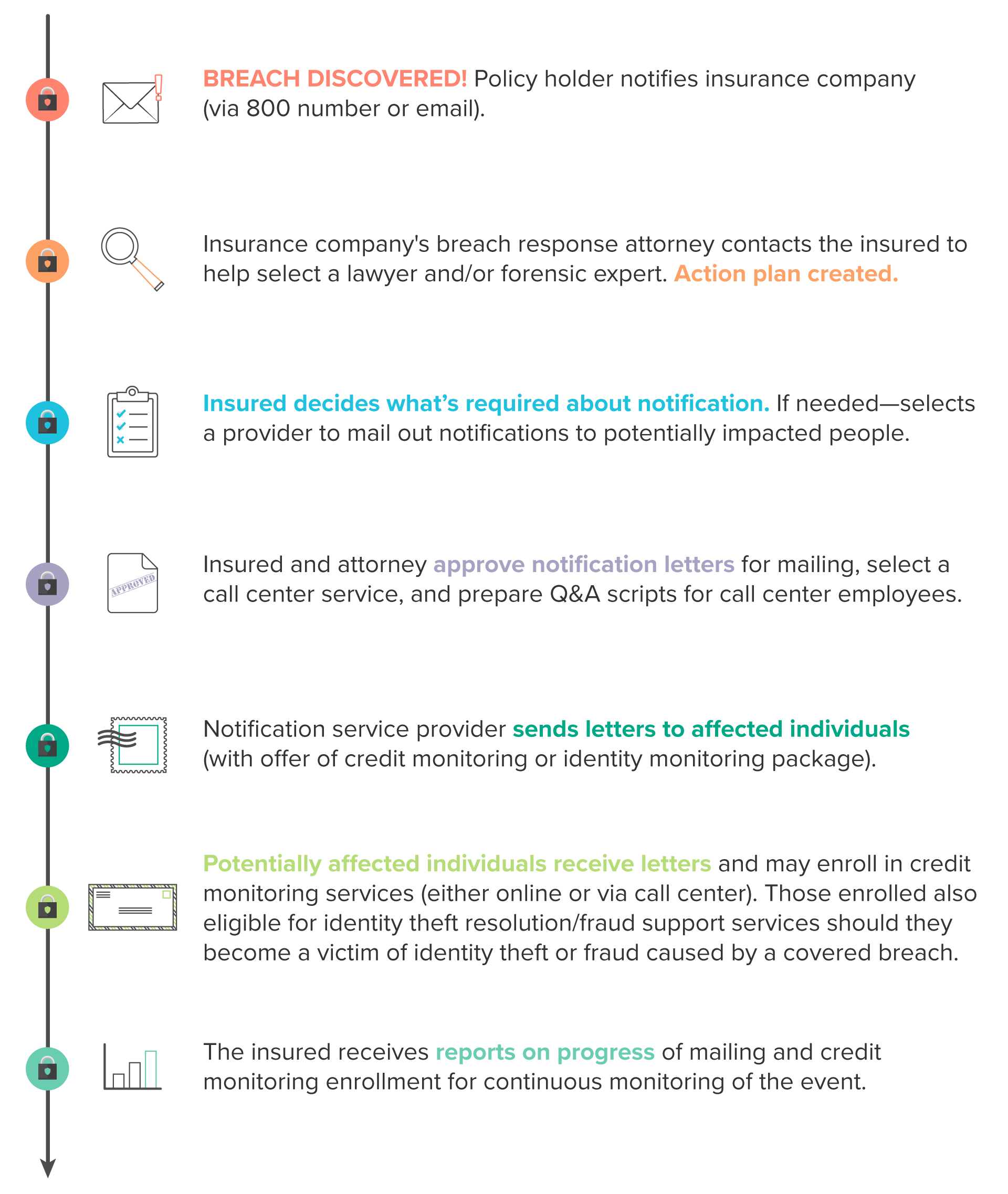
As far as the tactical steps after an incident, insurance carrier Beazley offers a sample timeline for what policyholders can expect should they uncover a breach:
The question of grounds for legal action doesn’t have a clear-cut answer, because it comes down to what courts see as “damages”—does the act of data being taken count? Or is it only once that data are used again?
“Plaintiffs have argued that merely having to go through the annoyance and cost of obtaining credit monitoring—in addition to the stress involved—constitutes damages,” says David Horrigan, e-discovery counsel and legal content director at kCura.
“Defendants have argued that if the data are not used to the plaintiffs’ detriment, for example opening a credit card and maxing it out, there are no damages,” says David. “Nevertheless, in Anderson v. Hannaford Bros. Co., the US Court of Appeals for the First Circuit held that credit monitoring can constitute damages.”?
However, other courts have gone the other way.? In In re Anthem Data Breach Litig., the court held that under New York law, damages resulting from the “probability” data might be used are not recoverable.
2. How often do companies make claims on their policies?
“Not as often as you’d think—given what you hear in the news—though companies are required to report small or even potential breaches,” says Erica Rangel, a broker at RT Specialty.
Notification of incidents happens more often. No matter the size of the group potentially affected, the organization is obligated to notify all people involved.
“With a cyber policy, the trigger is the breach, not a reported claim,” says Erica. “So once the carrier knows about the breach, the policy starts responding.”
Notification under the policy can be triggered without the filing of a formal claim. A company may later make a claim if there’s evidence that shows any personally identifiable information stolen was used to take further action, like open new accounts.
In general, the number of third-party claims against the policy is much fewer than the breaches reported and triggering notification and credit monitoring.
3. How long does it take for a company to discover a breach?
It can take weeks or months before a company discovers a breach, so policyholder claims could come long after an incident.
The Ponemon Institute’s 2017 Cost of Data Breach Study found, not surprisingly, that the faster a data breach can be identified and contained, the lower the costs.
And the source of the breach influences the speed at which it’s discovered.
According to the study, which included 419 global companies, the mean time to identify a breach was 191 days, and another 66 days on average to contain it. Malicious and criminal attacks had the highest times to identify and contain (214 and 77 days, respectively), while those caused by human error had the lowest (168 and 54 days, respectively).
This is where good information governance practices are key—knowing what data you have and where they reside.
The e-discovery tools you’re already using can be invaluable for protective measures like data classification and data store identification. In the case of a breach, these tools can also help you find personally identifiable information in the stolen data set; if the breach happened due to internal factors, these tools can help identify actors, review and analyze employee communications and documents, analyze social networks to uncover potential co-conspirators, and more.
4. What does a breach typically cost a company?
The average total cost of a data breach in 2016 was $3.62 million (a decrease from $4 million in 2015). The average cost for each lost record of sensitive information dipped to $141 from $158 in 2016—though the size of data breaches themselves is up 1.8 percent, according to the Ponemon study.
5. How much must a company consider breach risks with their vendors?
Each company’s risk profile will be different based on the intricacies of its business, including vendor relationships, which add another layer of vulnerability. Also, “if a company maintains an active social media presence, it will want media liability coverage. And as more regulations are enacted around cybersecurity and data-handling practices, coverage for regulatory fines is increasing in importance for many entities,” adds Judy.
We saw an example of third-party vulnerability in Target’s 2014 breach affecting 110 million customers. Using pilfered credentials from an HVAC vendor, hackers entered Target’s billing and contracts systems; from there, they made their way into the company’s point of sale systems, which house customers’ payment and personal information.
6. Does having a breach make it more difficult for a company to secure future coverage?
“Coverage after a breach is certainly obtainable, but premiums can increase significantly depending on what the carrier had to pay out,” says Erica.
With the string of large-scale retail breaches a few years back, there was a backlash against the industry for a while, which has since lifted.
The Ponemon Institute’s study found that the larger the data breach an organization has had, the less likely it is that it’ll have another breach in the next 24 months. Based on the experiences of organizations in their research, the probability of a data breach can be predicted based on two factors: how many records are lost or stolen and where the organization is located.
7. Are there any factors that positively affect a breach situation?
Yes. The survey found that several factors had positive influence during a breach in terms of reducing per capita cost; the top three were:
- Having an incident response team in place
- Extensive use of encryption
- Employee training
Just one piece of the complex cybersecurity puzzle, “having insurance protection” ranked in at number 9 out of 20 factors.
Cyber coverage is a safety net in case catastrophe strikes. As with our own health, preventative care and smart but small day-to-day decisions, like building an incident response team, making encryption the norm, taking employee training seriously, can make the biggest difference in protecting your organization’s cyber health—as well as remaining a steadfast link in your clients’ cyber networks.
April Runft is a member of the marketing communications team at Relativity, specializing in content development.










